Hey dear lxj2007499,
The reason is, the RFC connection NPL_BGRFC_DEST is not working properly.
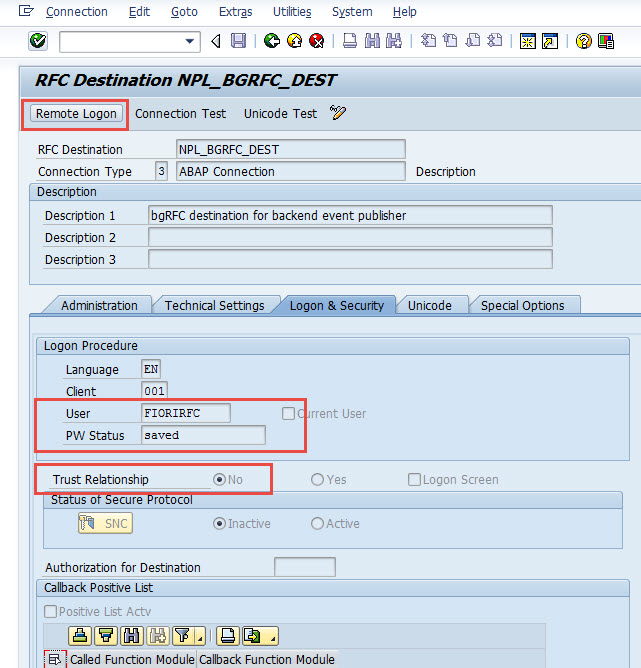
When you check the definition of NPL_BGRFC_DEST, you'll see it's not a trusted connection, and hard coded with user name FIORIRFC with password. When you try testing 'Remote login', it popped up a logging screen which is not correct
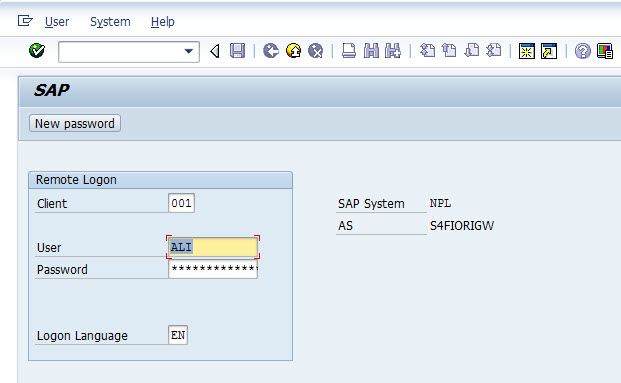
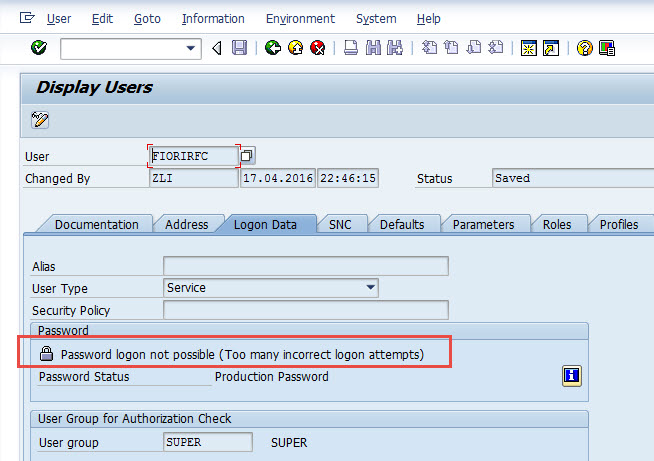
Now when you go to NPL to check the user FIORIRFC, you'll see it was locked due to incorrect login
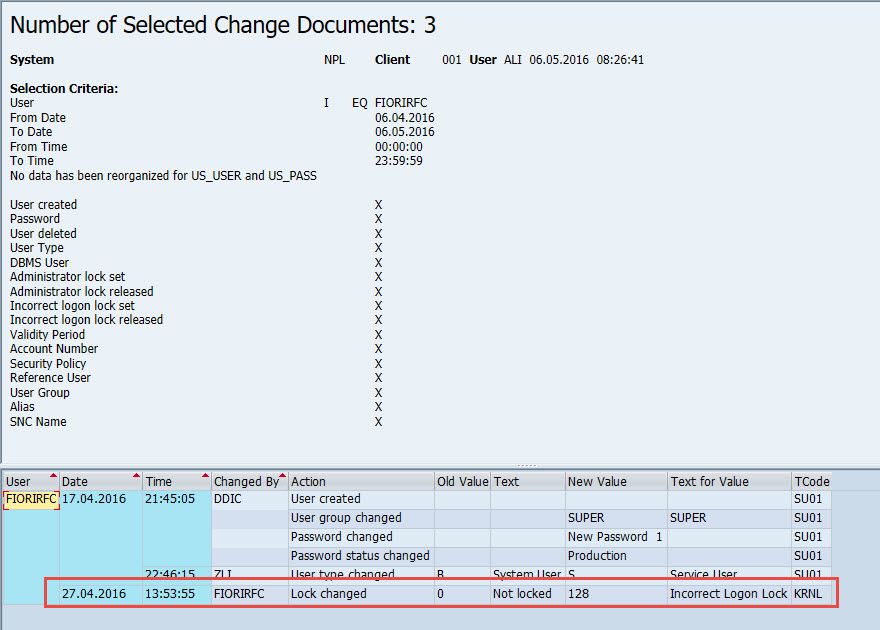
Checked the user change history to see when it was locked, which was long time ago on Apr. 27th
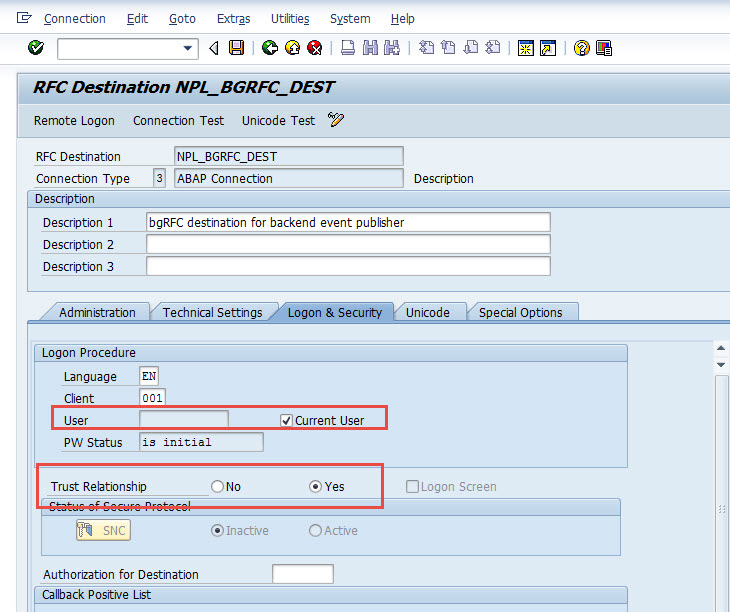
Considering this user FIORIRFC has high privilege and was defined as a service type of user, so at this time we don't want to unlock it. Instead you may want to use the trusted RFC from A4H to connect to NPL, so here I'll change the RFC NPL_BGRFC_DEST to trusted RFC
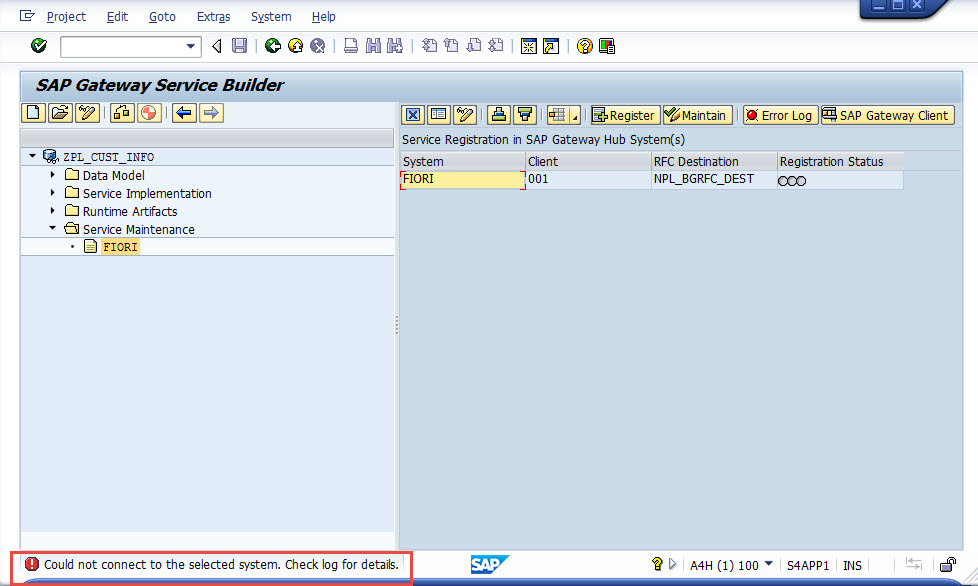
Now testing the SEGW again, still failed
Check the logs
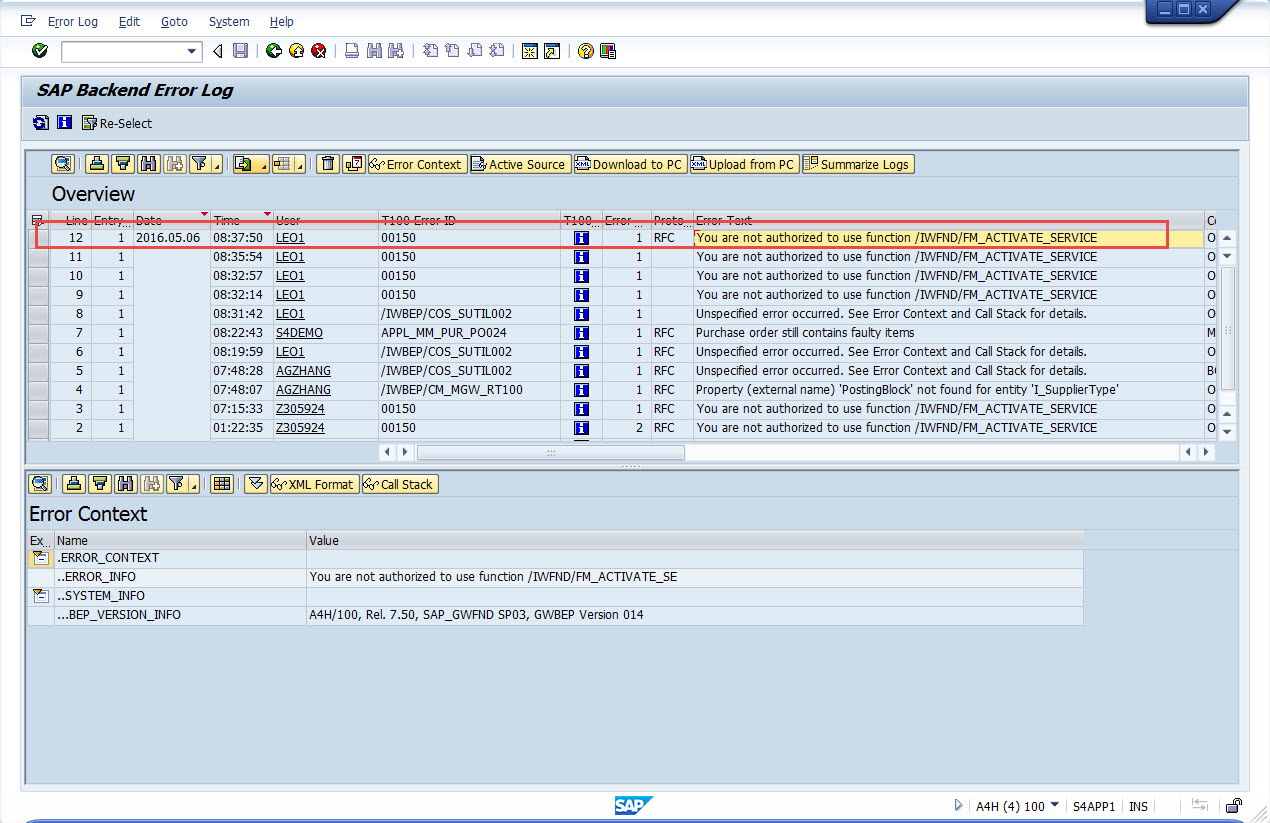
So missing authorizations. Now we add these authorization into the roles. Please note that when the user LEO1 try to register gateway from A4H, the actual authorization failure is happening in the target system that connected via RFC, which is NPL
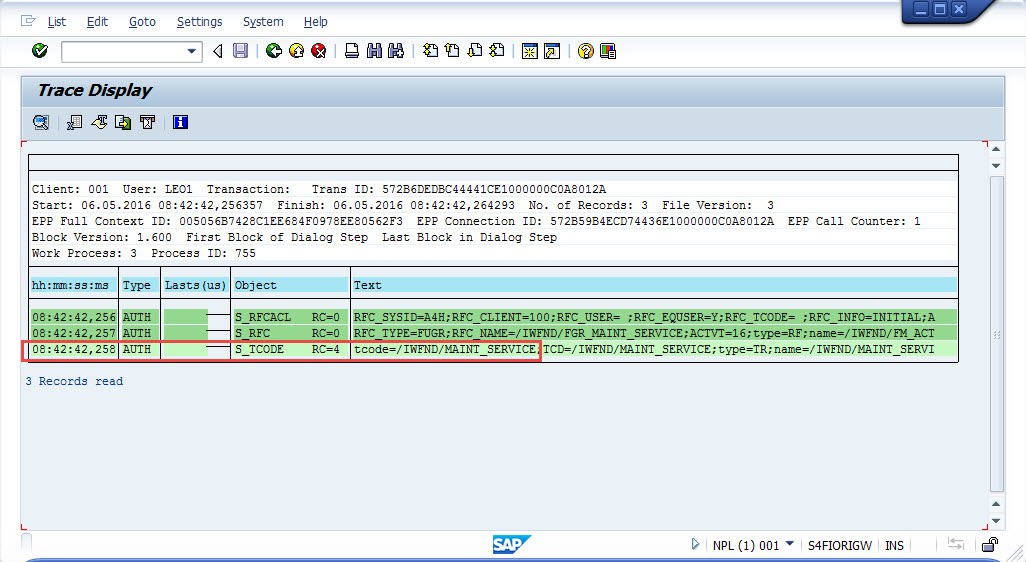
Add the authorization to NPL developer role
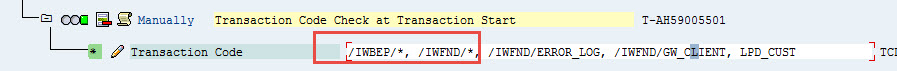
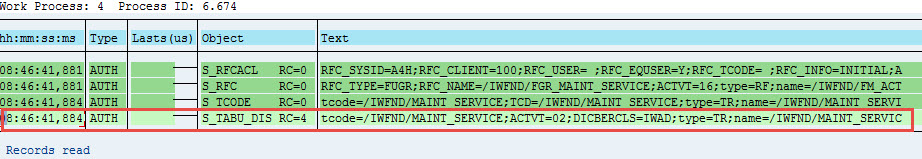
Now retry SEGW in A4H, still failed, missing following authorization about table maintenance
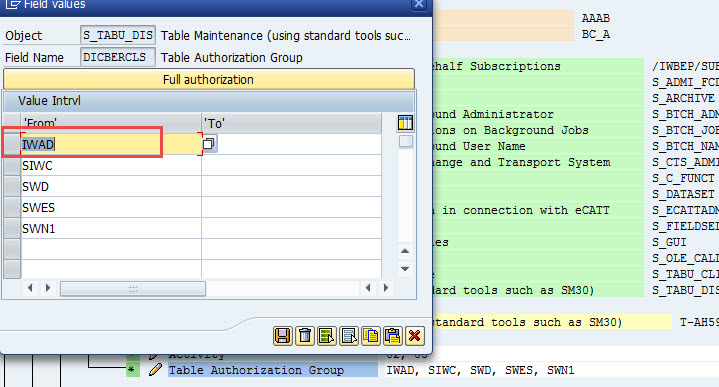
We have no concerns to allow developers to change all these tables. So add auth group IWAD into S_TABU_DIS
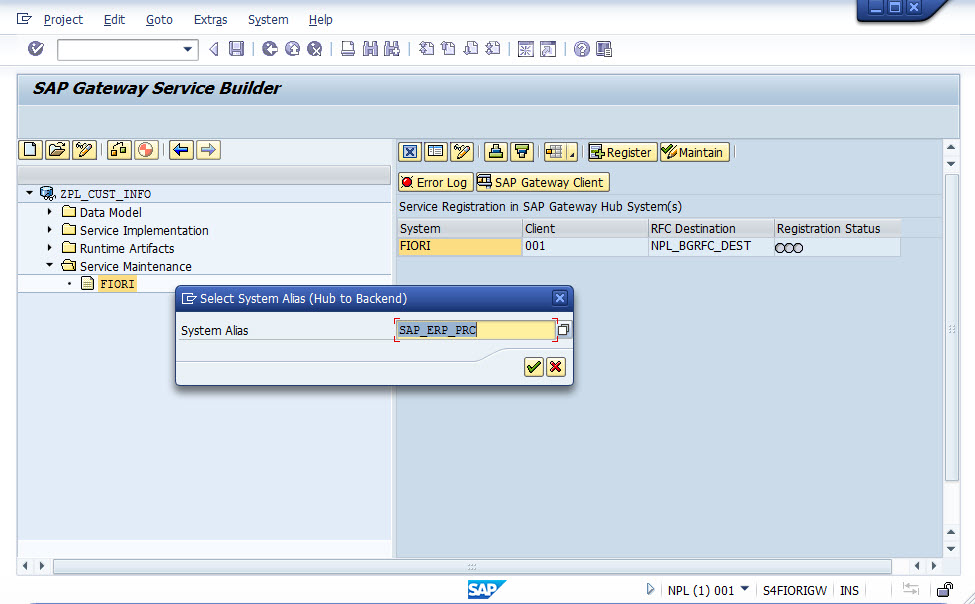
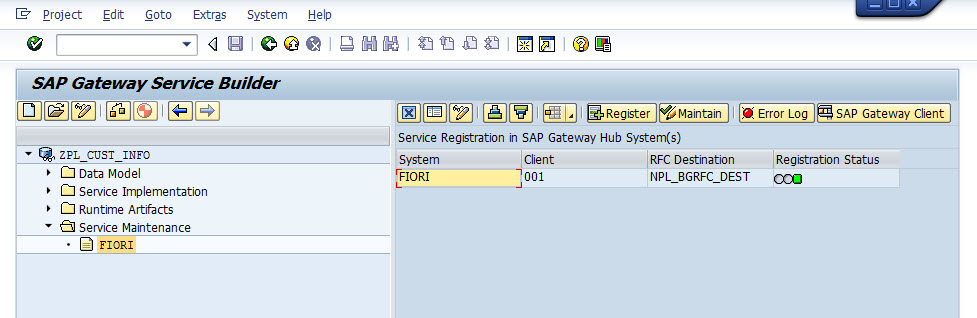
Now try SEGW again in A4H, finally successful.
Hey dear lxj2007499,
The reason is, the RFC connection NPL_BGRFC_DEST is not working properly.
When you check the definition of NPL_BGRFC_DEST, you'll see it's not a trusted connection, and hard coded with user name FIORIRFC with password. When you try testing 'Remote login', it popped up a logging screen which is not correct


Now when you go to NPL to check the user FIORIRFC, you'll see it was locked due to incorrect login

Checked the user change history to see when it was locked, which was long time ago on Apr. 27th

Considering this user FIORIRFC has high privilege and was defined as a service type of user, so at this time we don't want to unlock it. Instead you may want to use the trusted RFC from A4H to connect to NPL, so here I'll change the RFC NPL_BGRFC_DEST to trusted RFC

Now testing the SEGW again, still failed

Check the logs

So missing authorizations. Now we add these authorization into the roles. **Please note that when the user LEO1 try to register gateway from A4H, the actual authorization failure is happening in the target system that connected via RFC, which is NPL**

Add the authorization to NPL developer role

Now retry SEGW in A4H, still failed, missing following authorization about table maintenance

We have no concerns to allow developers to change all these tables. So add auth group IWAD into S_TABU_DIS

Now try SEGW again in A4H, finally successful.
















